Cryptography is defined as the process of the converting the readable plain text into intelligible data or vice versa in order to protect the information. It is the method of data sharing between two people in such a manner that the person who is supposed to read the data can only have access to it.
With various techniques introduced, the criminals trace the path of the data and steal the information in the mid-way. Therefore, using cryptography the data remains intact during the procedure and is readable at the two ends of the communication channel.
Type of Cryptography:-
Cryptography is widely known to exist in three forms,
1. Symmetric encryption – In this encryption technique, the data is transmitted between two parties if they have shared a secret private key. The same key is utilized to encrypt as well as decrypt the data in a readable format. This ensures that no other individual can get a peep into the information if he does not have access to the keys.
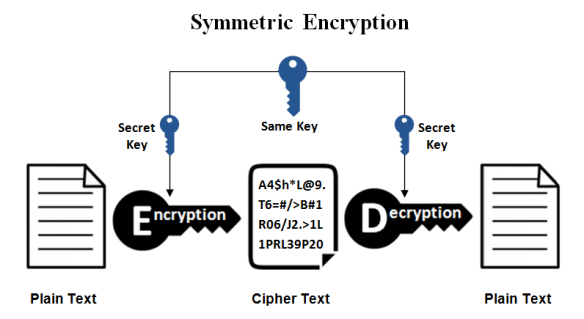
This method has the disadvantage of the key being shared among every member of the group who needs hands on the information. Unless all have exchanged the same key, the data cannot be converted into the original text again.
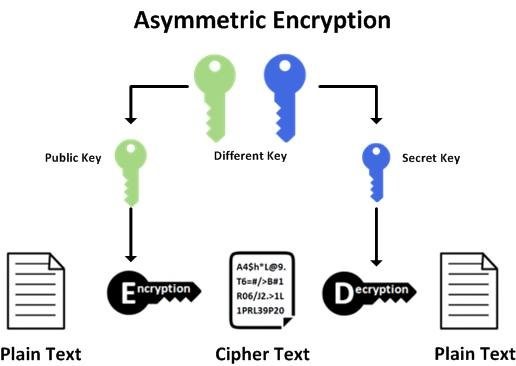
2. Asymmetric encryption – This technique, however, uses two keys in the encryption-decryption process. One is private key and the other is a public key. The public key is used to encrypt the data and is available to everyone on the internet without security.
On the other hand, the private is used to decrypt the data and is kept private. Without the access of the private key, one cannot convert the complex text into plain and readable text.
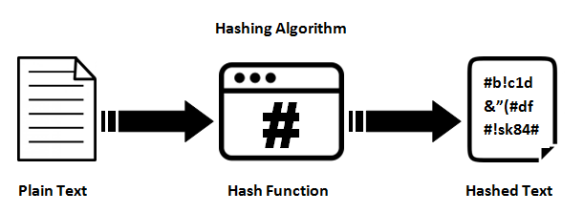
3. Hashing Functions – The main difference with this technique is it does not use any key to for the cryptography procedure. Instead, it uses a hash function of the length of the plain text. This makes it almost impossible to trace back the original text.
Many of the computer security software developers have studied and found that many of the viruses and malware techniques also use encryption procedure to track and store that data for harmful purposes.
